Snort on Debian
Snort, is an Intrusion Detection and Prevention System for Windows and *nix machines. You can download it from here: Snort Download.
Well, for debian we dont require to download it from there. The command to download and install it is-
# apt-get install snort
This will download and install Snort to your Debian.
Next step is to configure the Snort for generating alerts for any activity. For example, we can consider ICMP-ping requests for alerts. Whenever someone pings our machine, an alert will be logged.
For configuration, 3 directories are necessary. If they are not created on their own, create them with mkdir command. They are:
/etc/snort
/etc/snort/rules
/var/log/snort
Now, our configuration file is: /etc/snort/snort.conf
If you need, you can take a backup of the original file, and then create a new file and edit it as below:
include /etc/snort/rules/icmp.rules
We don’t need to add other lines, as right now we are considered about only the ICMP requests, we will configure only the icmp.rules file and hence it is referenced in the snort.conf file.
Now, the icmp.rules file contains the below content:
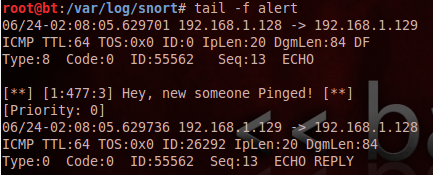
alert icmp any any -> any any (msg:”Hey, someone pinged!”; sid:477; rev:3;)
This line will log any ICMP request from any source, with the given message. The sid and rev are used to uniquely identify Snort rules and its revisions.
Now, to start Snort listening on interface eth1, the command will be:
# snort -c /etc/snort/snort.conf -l /var/log/snort -i eth1
The first location is where the Snort configuration file is located, while the second location with -l is where to store the alert, and -i provides the interface selection.
Now, ping the machine from some other machine, and you will find an entry in the alert file located in /var/log/snort. It will contain the source and destination IP addresses, the time and date of the incident and other information related to the query.
Similarly, you can configure Snort to generate alerts on various incidents like FTP login, SSH attempts, Telnet requests.